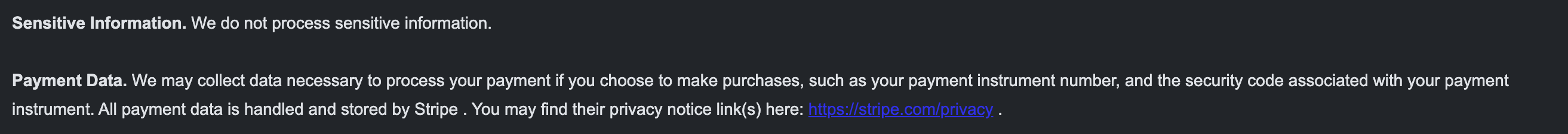
If you're curious btw this is my rules template i'm using. It's not fully complete but you can see the extent to which i've gone to make sure users can only use specific collections.
These need to be tested under different scenarios each time you make changes to the .rules file either manually or automatically to ensure they work.
I don't know if this has been done but i'm mentioning it because it seems like not much effort has been put into protecting the privacy of those who join the site
Either way. None of this matters at the moment because and i'll repeat... You don't have a working privacy policy!
Which means you need to either invite users to test, block specific regions from joining or take the site down.
These need to be tested under different scenarios each time you make changes to the .rules file either manually or automatically to ensure they work.
I don't know if this has been done but i'm mentioning it because it seems like not much effort has been put into protecting the privacy of those who join the site
Either way. None of this matters at the moment because and i'll repeat... You don't have a working privacy policy!
Which means you need to either invite users to test, block specific regions from joining or take the site down.
JavaScript:
rules_version = '2';
service cloud.firestore {
match /databases/{database}/documents {
// Match all documents
match /{document=**} {
// Lock down the database by default
allow read, write: if false;
}
match /users/{userId} {
// Updates are possible if the user owns the collection & isn't updating the valus of any locked keys
allow update: if isAuthenticated()
&& isOwner(userId)
&& isNotBanned()
&& isTimestampValidated()
&& lockKeys(['created', 'subscriptions']);
}
// Check a user has signed in and has verified their email
function isAuthenticated() {
return request.auth.uid != null && request.auth.token.email_verified == true;
}
// Check if the user is an owner from the name of the document or by the uid in the resources data
function isOwner(userId) {
return request.auth.uid == userId || request.auth.uid == resource.data.author_uid;
}
function isNotBanned() {
return exists(/databases/$(database)/documents/bans/$(request.auth.uid)) == false;
}
// Prevent timestamp spoofing
function isTimestampValidated() {
return request.time == request.resource.data.created;
}
// Lock certain keys so they can only be updated by serverside functions
function lockKeys(keysNotAllowed) {
return request.resource.data.diff(resource.data).affectedKeys().hasOnly(keysNotAllowed) == false;
}
}
}